Executive Summary
Open-Source Intelligence (OSINT) refers to the gathering and analyzing of publicly available data on individuals. While OSINT is widely used for legitimate purposes by law enforcement, researchers, threat hunting, and security teams, it has also become a favored technique for threat actors. As part of the reconnaissance phase, which is the first step in the cyber kill chain, attackers piece together fragments of data from the internet to build detailed profiles of organizations, their technology, and key individuals. This information is then weaponized to craft highly targeted and sophisticated attacks, from spear-phishing emails, social engineering, to technical exploits.
In fact, using OSINT as part of reconnaissance is the first step of any sophisticated campaign, allowing adversaries to gather data with no direct interaction. A good example of this is the MGM and Caesars Attack in 2023, where the threat actor, Scattered Spider, used data available on LinkedIn to impersonate IT support staff.
The risks posed by OSINT-driven attacks must be considered business critical. An expanded digital footprint (the sum of an organization’s online exposure) can expose employee names, emails, technology stack, and even sensitive data such as employee photo ID, essentially providing a roadmap for threat actors. A large footprint can also lead to the exposure of usernames and email addresses, by tying them back to data breaches, which threat actors leverage in brute-force or credential stuffing attacks, especially since almost half of users reuse passwords across accounts.
Publicly available details about key staff and executives (from LinkedIn, press releases, social media posts, etc.) fuel social engineering and business email compromise (BEC) campaigns, where criminals impersonate trusted parties to defraud the company. Social engineers thrive on OSINT, and even seemingly minor personal details can allow them to convincingly pose as colleagues or even trusted vendors. If an organization’s public data is abundant and unguarded, attackers can, and will craft hyper-personalized scams that are difficult to detect or resist.
The exposure of public data available to malicious OSINT practitioners can lead to both physical and reputational harm. High-profile company executives are often targets of doxing and cyber threat campaigns that publish home addresses, family details, and other personal data. A recent, and most sinister example of this was the murder of Brian Thompson in 2025, the CEO of UnitedHealthcare. The suspect had prior knowledge of Thompson’s whereabouts, and was seen at the New York Hilton Midtown hotel days before the attack which took place there. This incident highlights the vulnerabilities that company executives and public figures face, especially when their schedules are made public.
For organizations, other impacts of unmanaged OSINT risk can include:
- Financial losses: Fraud, scams, or competitive disadvantage
- Reputational damage: Leaks or misinformation spreading publicly
- Legal/compliance issues: When sensitive data like customer info is exposed
- Cybersecurity incidents: Enabled by leaked infrastructure details, or social engineering
Framework Positioning
The OSINT Defense & Security Framework (ODSF) is the worlds first OSINT risk management framework created by Ray Heffer and developed by PsySecure to systematically address the growing threat of adversaries weaponizing public information to target an organization’s most critical asset - its people. Designed and structured as a controls-based model, ODSF enables organizations to reduce their digital footprint, defend against OSINT-based reconnaissance, and safeguard against targeted attacks to the organization and personnel. ODSF also aligns with established standards like NIST CSF, ISO 27001, and Zero Trust. The ODSF fills a critical gap in enterprise defense strategies by treating open-source intelligence exposure as a primary attack vector.
The framework is openly licensed under CC BY-NC-SA 4.0 to promote collaboration and derivative innovation, while maintained and published by PsySecure, to preserve authorship integrity and version governance.
Framework Structure
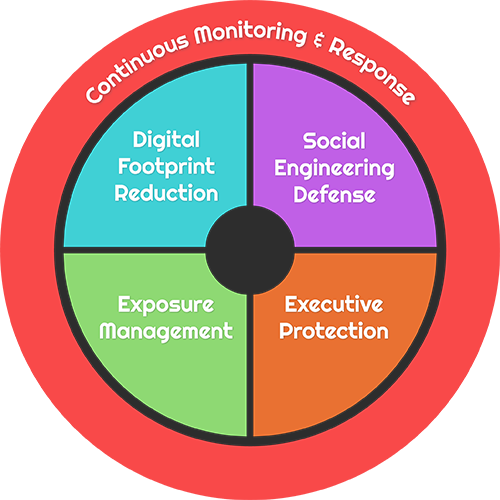
The OSINT Defense & Security Framework is organized into five distinct Focus Areas, each addressing a crucial aspect of OSINT based risk management:
Digital Footprint Reduction
Minimizing the public exposure of sensitive or critical information related to the organization and its people. This includes controlling what information appears in search results, social media platforms, and public databases. Organizations learn to systematically identify and reduce unnecessary data exposure while maintaining operational effectiveness.
Social Engineering Defense
Preparing defenses for the human element and processes to resist attacks leveraging OSINT. This encompasses security awareness training specifically focused on OSINT threats and establishing protocols to verify requests for sensitive information. Teams develop skills to recognize and respond to sophisticated social engineering attempts.
Technology Exposure Management
Controlling and hardening the organization's technical attack surface that is discoverable via OSINT tools. This includes managing publicly visible infrastructure details, service enumeration, and technology stack information. Organizations implement controls to reduce technical intelligence available to adversaries during reconnaissance.
Executive Protection
Special safeguards for high-profile individuals such as executives and board members who face elevated OSINT targeting and personal risk. This includes personal privacy protection, travel security, and reputation management. Comprehensive protection strategies address both digital and physical security considerations.
Continuous Monitoring and Response
Ongoing surveillance of public data for emerging threats or leaks, and the capability to respond rapidly. This includes monitoring for data breaches, leaked credentials, and emerging threat intelligence related to your organization. Organizations establish processes for detection, assessment, and mitigation of OSINT-based risks.
Each focus area is divided into subcategories (objectives or outcomes) and specific controls. The framework first outlines the core controls (ODSF Core) under each category (what needs to be done). Following the core, implementation guidance, examples, and tools (how to enact the controls) is provided. Throughout, insights from OSINT practitioners and security experts are incorporated, highlighting how attackers operate and how defenders can counteract them.
Implementation Philosophy
Maintaining a defensive posture with ODSF is not a one-time exercise, but an ongoing effort of assessment, reduction, monitoring, and adaptation. As one industry expert noted, “Smaller, well-managed digital footprints offer fewer opportunities for exploitation”. Organizations are therefore advised to treat OSINT risk management as a continuous process, changing the organizational mindset.
By regularly applying the controls in this framework, organizations can stay ahead of attackers that use OSINT for the offensive, making it significantly harder for malicious actors to find useful information and mount successful attacks.
By integrating ODSF into an organization’s security strategy, they can reduce OSINT-based risks to reputation, finances, and most importantly, the people.
– Ray Heffer
Getting Started
Ready to implement the OSINT Defense & Security Framework in your organization? Contact PsySecure to learn how ODSF can be tailored to your specific risk profile and business requirements.
Further Reading
To learn more about OSINT threats and defensive strategies: